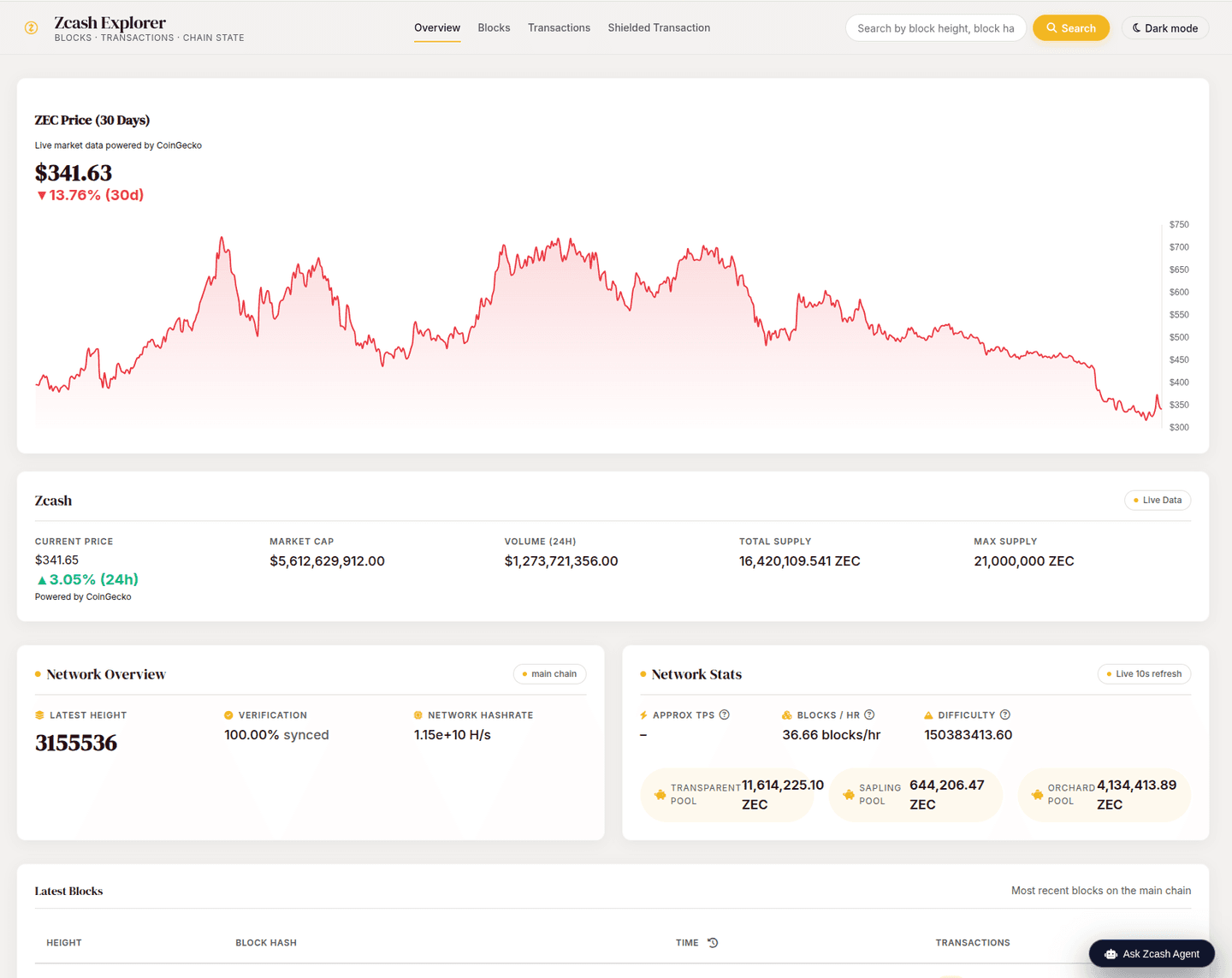
Zcash explorer
explorer
Created on 2nd December 2025
•
Zcash explorer
explorer
The problem Zcash explorer solves
The Challenge in Zcash Ecosystem
Zcash's privacy features create a critical usability gap: users cannot easily view or verify their own shielded transactions. Traditional block explorers only show transparent transactions, creating major pain points:
- No transaction visibility without running a full node
- Difficult auditing for accounting and compliance
- Forced trade-off between privacy and transparency
- High technical barrier requiring node operation and RPC knowledge
- Limited insights into shielded pool adoption and network health
The Solution
Client Side Shielded Transaction Decryption:
Users bring their viewing keys to decrypt shielded transactions entirely in-browser with zero server involvement, while preserving network-wide privacy.
Real-Time Network Analytics:
Dashboards display network health, shielded pool balances, transaction throughput, and mining difficulty, making Zcash data accessible without technical expertise.
AI-Powered Blockchain Assistant:
Natural language queries replace complex RPC commands, enabling anyone to extract blockchain insights instantly.
Open Source Developer Infrastructure:
Reference implementations for client-side decryption, RPC integration, and privacy preserving architecture accelerate Zcash application development.
Who Benefits
- Individual Users: Audit shielded transactions without compromising privacy
- Businesses: Verify private transactions for accounting and compliance
- Developers: Build privacy preserving applications using proven patterns
- Researchers: Analyze network data and adoption trends
- Zcash Ecosystem: Lower barriers to shielded transaction adoption
This explorer makes privacy practical,proving users can have both transparency and privacy. By keeping decryption client side and making shielded transactions accessible, it advances Zcash's mission of financial privacy for everyone.
Challenges we ran into
Limited Zcash Documentation & Resources:
The biggest challenge was the scarcity of comprehensive developer documentation for Zcash's shielded transaction decryption. Unlike more mainstream blockchains, Zcash has limited tutorials, SDK examples, and community resources for building client side decryption tools.
Solution: We dove deep into the official Zcash protocol specifications, studied existing open source wallets, and reverse engineered cryptographic implementations to understand how viewing keys work with Sapling and Orchard pools. This required piecing together information from multiple sources including ZIP (Zcash Improvement Proposal) documents and the Zcash Rust crates.
RPC Connection & Data Consistency Issues:
Working with Zcash node RPC endpoints presented several hurdles:
Inconsistent data formats across different RPC methods
Rate limiting and timeout issues when querying large block ranges
Solution: We implemented robust error handling, caching layers, and fallback mechanisms. We also added sync status indicators to inform users when data might be outdated.
AI Agent Integration Complexity:
Integrating an AI assistant that could accurately answer Zcash specific questions required extensive prompt engineering and context management to avoid hallucinations about blockchain data.
Solution: We implemented structured data retrieval patterns and validation layers to ensure the AI agent only provides factual information.
These challenges taught us that building privacy preserving applications requires not just technical skill, but a deep commitment to the privacy principles that make projects like Zcash essential.
Tracks Applied (7)
General Bounty
Network School
Privacy-Preserving AI & Computation
Axelar Network
Zcash Data & Analytics
Gemini
Privacy Infrastructure & Developer Tools
Zcash Community Grants
Zcash Data & Analytics
Raybot
Privacy Infrastructure & Developer Tools
Raybot
General Bounty
Project Tachyon
Cheer Project
Cheering for a project means supporting a project you like with as little as 0.0025 ETH. Right now, you can Cheer using ETH on Arbitrum, Optimism and Base.